ClickPoint is Enterprise Ready Software as a Service
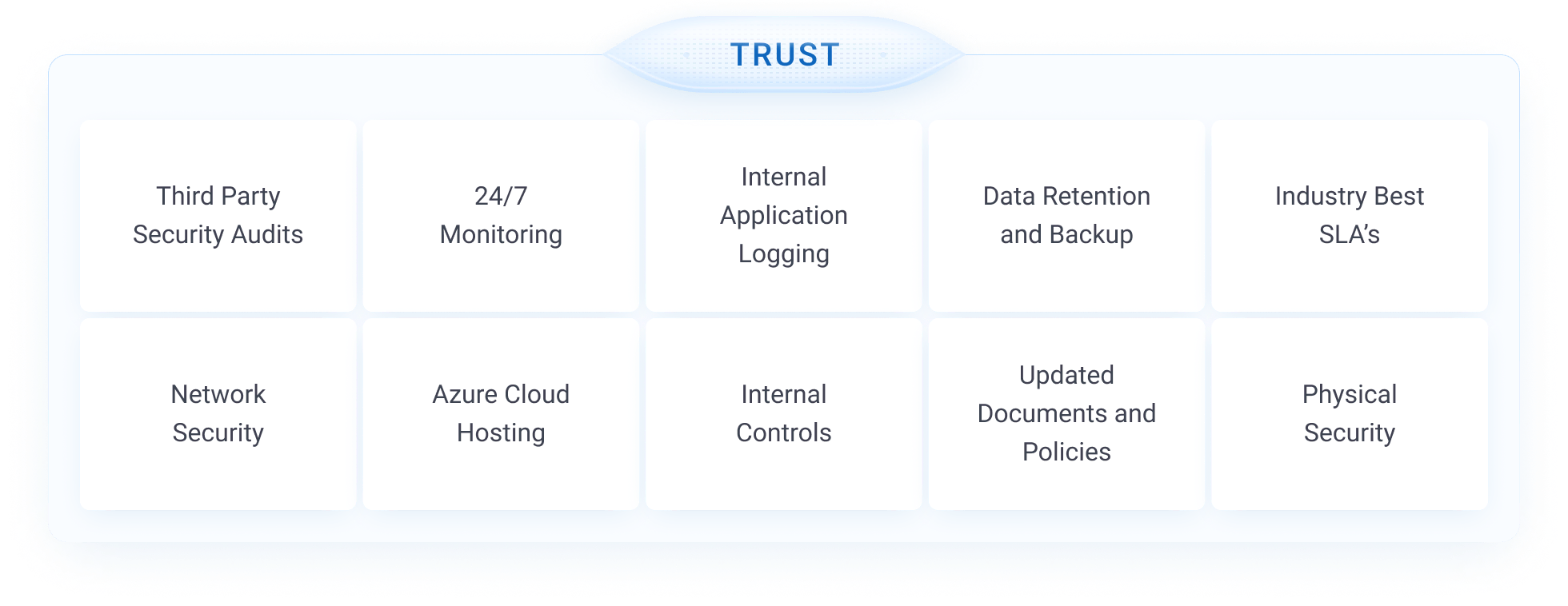
Security and Reliability Commitment
ClickPoint invests in partnerships with reputable and trusted security solutions. The ClickPoint data security, privacy, data retention, and reliability assurances are outlined below. Upon request, ClickPoint can provide additional documentation as needed.